
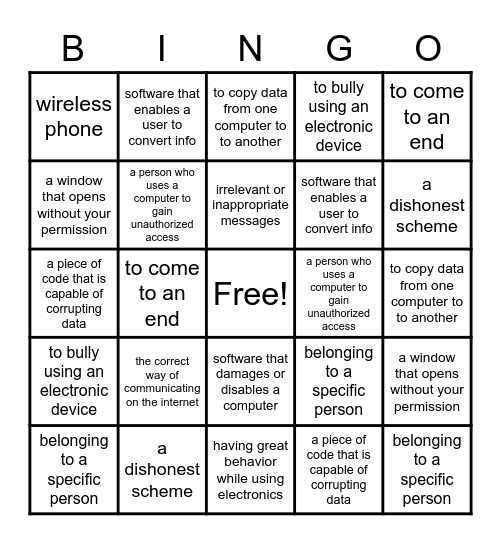
This bingo card has a free space and 24 words: belonging to a specific person, the correct way of communicating on the internet, irrelevant or inappropriate messages, a piece of code that is capable of corrupting data, to come to an end, wireless phone, software that enables a user to convert info, to copy data from one computer to to another, a person who uses a computer to gain unauthorized access, to copy data from one computer to to another, a piece of code that is capable of corrupting data, a person who uses a computer to gain unauthorized access, belonging to a specific person, a window that opens without your permission, a window that opens without your permission, a dishonest scheme, having great behavior while using electronics, to bully using an electronic device, a dishonest scheme, to bully using an electronic device, to come to an end, software that damages or disables a computer, software that enables a user to convert info and belonging to a specific person.
⚠ This card has duplicate items: belonging to a specific person (3), a piece of code that is capable of corrupting data (2), to come to an end (2), software that enables a user to convert info (2), to copy data from one computer to to another (2), a person who uses a computer to gain unauthorized access (2), a window that opens without your permission (2), a dishonest scheme (2)
Technology Terms | Technology Bingo | Ingredients to Software | CYBERSECURITY BINGO | Computer Concepts
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.