
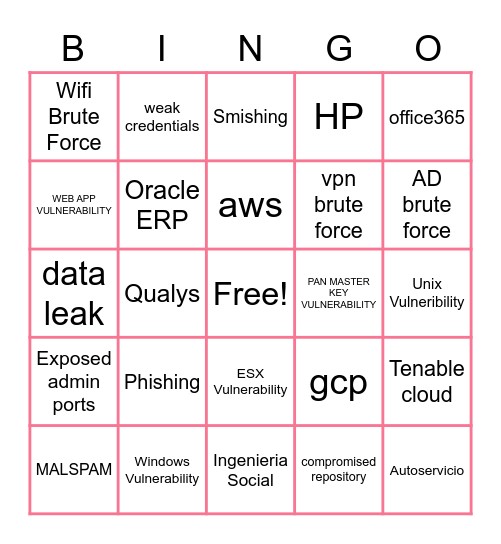
This bingo card has a free space and 24 words: Phishing, Windows Vulnerability, aws, MALSPAM, office365, Wifi Brute Force, WEB APP VULNERABILITY, weak credentials, PAN MASTER KEY VULNERABILITY, ESX Vulnerability, vpn brute force, data leak, gcp, Tenable cloud, Oracle ERP, compromised repository, Unix Vulneribility, Smishing, AD brute force, Qualys, Autoservicio, Exposed admin ports, HP and Ingenieria Social.
Cybersecurity | SECURITY BINGO | Cyber Bingo | Cyber Bingo! | Cyber Bingo
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.