
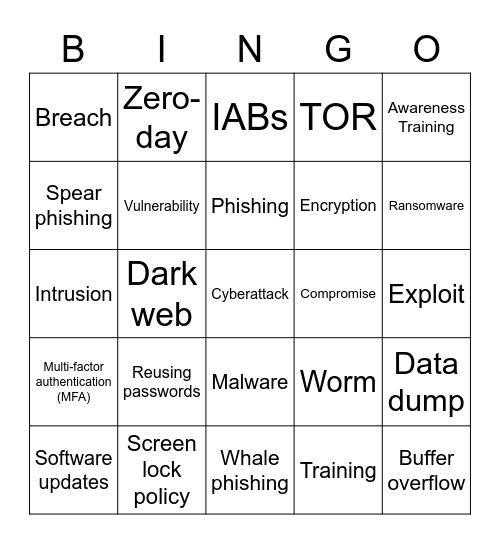
This bingo card has a free space and 24 words: Reusing passwords, Screen lock policy, Phishing, Software updates, Awareness Training, Breach, Spear phishing, Zero-day, Compromise, Malware, Encryption, Intrusion, Worm, Data dump, Vulnerability, Training, Exploit, IABs, Ransomware, Dark web, Buffer overflow, Multi-factor authentication (MFA), TOR and Whale phishing.
Cybersecurity Bingo | Cybersecurity Bingo | Cybersecurity Bingo | Cybersecurity Bingo | CyberBINGO
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.