
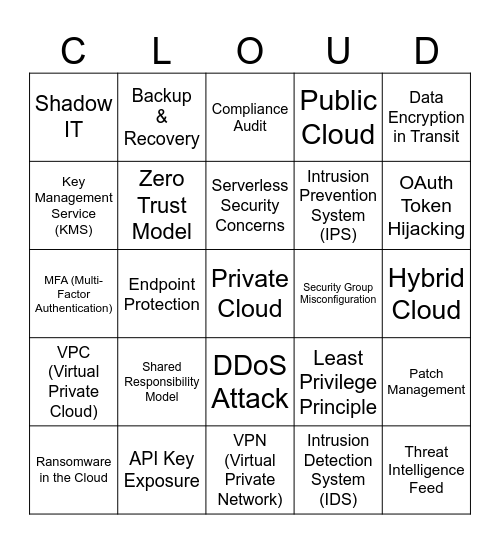
This bingo card has 40 words: IAM (Identity and Access Management), MFA (Multi-Factor Authentication), S3 Bucket Misconfiguration, Zero Trust Model, API Key Exposure, DDoS Attack, Serverless Security Concerns, Data Encryption at Rest, Data Encryption in Transit, VPC (Virtual Private Cloud), Endpoint Protection, Public Cloud, Private Cloud, Hybrid Cloud, Security Group Misconfiguration, Shared Responsibility Model, Cloud Access Security Broker (CASB), Shadow IT, Container Vulnerabilities, Compliance Audit, Patch Management, Intrusion Detection System (IDS), Intrusion Prevention System (IPS), Key Management Service (KMS), Network Segmentation, Data Residency Issues, Cloud-native Security Tools, CSPM (Cloud Security Posture Management), Threat Intelligence Feed, Ephemeral Infrastructure, Phishing Attempt, Ransomware in the Cloud, Incident Response Plan, Least Privilege Principle, OAuth Token Hijacking, VPN (Virtual Private Network), Security by Design, Logging & Monitoring, Backup & Recovery and Cloud Misconfiguration.
Essential Cybersecurity Terms | Cyber Awareness | Cyber Awareness | Cyber Bingo | Cyber Bingo
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.