
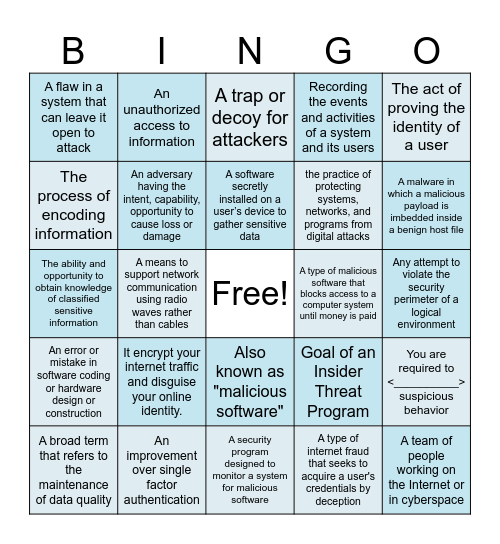
This bingo card has a free space and 24 words: It encrypt your internet traffic and disguise your online identity., An improvement over single factor authentication, A software secretly installed on a user’s device to gather sensitive data, A broad term that refers to the maintenance of data quality, The act of proving the identity of a user, A flaw in a system that can leave it open to attack, The process of encoding information, An unauthorized access to information, A type of malicious software that blocks access to a computer system until money is paid, Also known as "malicious software", the practice of protecting systems, networks, and programs from digital attacks, The ability and opportunity to obtain knowledge of classified sensitive information, Goal of an Insider Threat Program, You are required to <__________> suspicious behavior, An adversary having the intent, capability, opportunity to cause loss or damage, A type of internet fraud that seeks to acquire a user's credentials by deception, Any attempt to violate the security perimeter of a logical environment, A trap or decoy for attackers, A malware in which a malicious payload is imbedded inside a benign host file, A means to support network communication using radio waves rather than cables, A team of people working on the Internet or in cyberspace, An error or mistake in software coding or hardware design or construction, Recording the events and activities of a system and its users and A security program designed to monitor a system for malicious software.
Cybersecurity Bingo | UMA IT Cybersecurity Bingo | CYBERSECURITY BINGO | Security Bingo | Technology Terms
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.