
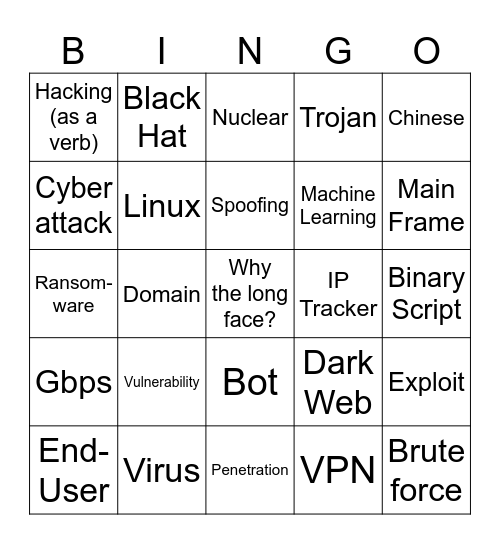
This bingo card has a free space and 48 words: Phishing, Brute force, Malware, Penetration, Vulnerability, Cloud, Black Hat, Anonymous, Cyber attack, AI, Linux, Trojan, Exploit, Dark Web, Root, Spam, Spoofing, IP Tracker, Zero-Day, Chinese, Domain, VPN, Hacking (as a verb), Machine Learning, Next-Gen, Main Frame, End-User, Data Logs, Bot, Gbps, Bug, Patch, Encryption, Extortion, Virus, Intelligence, 1337, Binary Script, admin, White Hat, Social Media, Legacy, Nuclear, Cyber, Ransom-ware, Breach, Unix and Keylogger.
6969Boiiii!!!1!!1! Presents CSI:Cyber | 6969Boiiii!!!1!!1! Presents CSI:Cyber | 6969Boiiii!!!1!!1! Presents CSI:Cyber | 6969Boiiii!!!1!!1! Presents CSI:Cyber | 6969Boiiii!!!1!!1! Presents CSI:Cyber
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.