
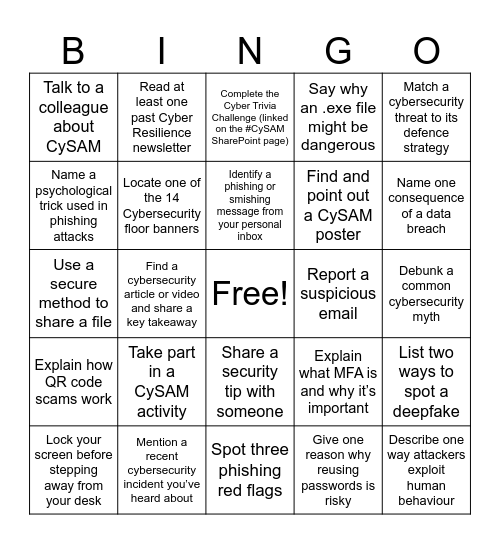
This bingo card has a free space and 25 words: Take part in a CySAM activity, Spot three phishing red flags, Identify a phishing or smishing message from your personal inbox, Lock your screen before stepping away from your desk, Match a cybersecurity threat to its defence strategy, Talk to a colleague about CySAM, Name a psychological trick used in phishing attacks, Read at least one past Cyber Resilience newsletter, Report a suspicious email, Share a security tip with someone, Find and point out a CySAM poster, Use a secure method to share a file, Explain what MFA is and why it’s important, List two ways to spot a deepfake, Locate one of the 14 Cybersecurity floor banners, Collect a pack of “Whoops” post-it notes from the Cyber Resilience Team, Debunk a common cybersecurity myth, Complete the Cyber Trivia Challenge (linked on the #CySAM SharePoint page), Name one consequence of a data breach, Find a cybersecurity article or video and share a key takeaway, Describe one way attackers exploit human behaviour, Mention a recent cybersecurity incident you’ve heard about, Explain how QR code scams work, Say why an .exe file might be dangerous and Give one reason why reusing passwords is risky.
Cybersecurity Bingo | Cyber Bingo | Banter BOOKO | Banter Booko | SCS Discover
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.