
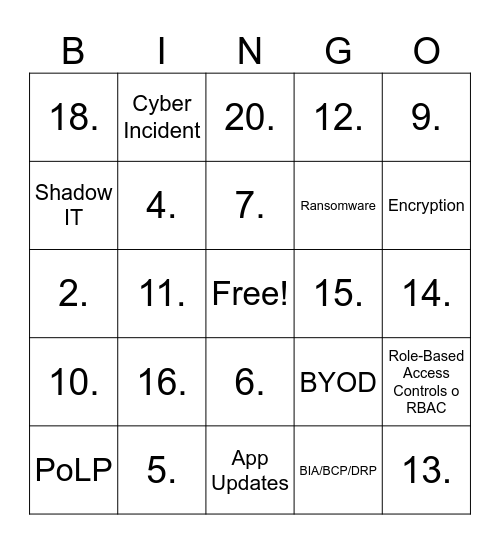
This bingo card has a free space and 40 words: 1., 2., 3., 4., 5., 6., 7., 8., 9., 10., 11., 12., 13., 14., 15., 16., 17., 18., 19., 20., Role-Based Access Controls o RBAC, BIA/BCP/DRP, Ransomware, Shadow IT, Audit Trail, Data Classification, DLP, Data Breach, Third Party Vendor Management, Patch Management, IT Risk Assessments, PoLP, Backups, BYOD, Encryption, App Updates, Al, Vul Scans, Cyber Incident and Phishing.
SPEAK DATA | SPEAK DATA | SPEAK DATA | SPEAK DATA | SPEAK DATA
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.