
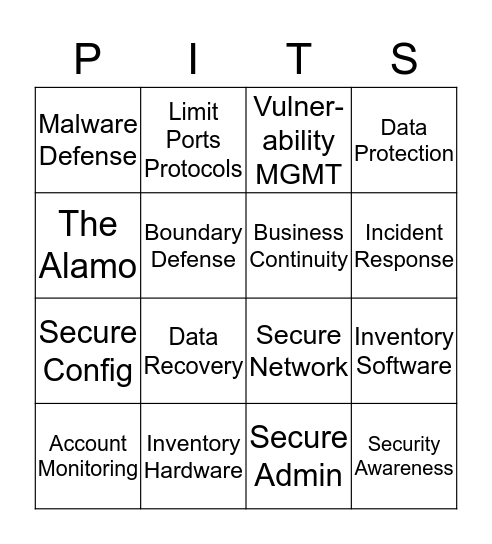
This bingo card has 16 words: Inventory Hardware, Inventory Software, Vulner-ability MGMT, Malware Defense, Secure Config, Limit Ports Protocols, Secure Network, Secure Admin, The Alamo, Boundary Defense, Account Monitoring, Data Protection, Data Recovery, Incident Response, Business Continuity and Security Awareness.
Practical IT Security | Tokes Bingo | Cybersecurity Awareness | Let's Play EC Bingo! | Breaches and Bingo
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.