
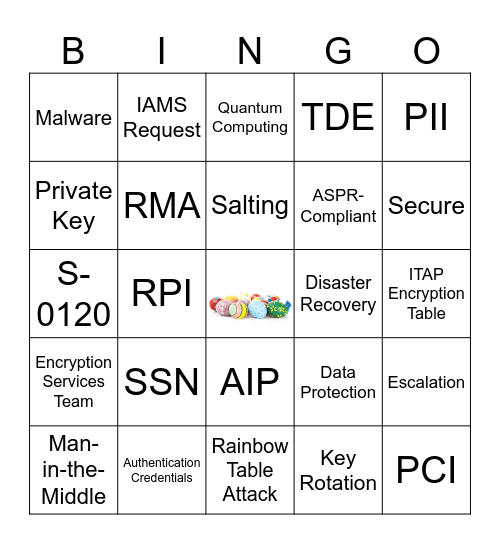
This bingo card has a free space and 75 words: CCRC Scorecard, Firewall, Quantum Computing, SSL, Data-at-Rest, Data-In-Transit, SecureData, AES, TLS, Hash Encryption, Encryption Keys, Symmetric Encryption, Salting, Private Key, SPI, RPI, SCD, PCI, Internet-Facing, PII, ASPR, S-0120, RMA, IAMS Request, TDE, Azure SSE, Azure Key Vault, DPI, ITAP, Privacy, Data Breach, GDPR, Cyberattack, Data Protection, Secure, ASPR-Compliant, Missing Encryption, Not Encrypted, ITAP Encryption Table, Key Rotation, Quantum-Safe Algorithm, NIST, End-to-End Encryption, Dark Web, Hacker, Ransomware, Man-in-the-Middle, Malware, Decryption, VPN, MFA, AIP, Brute-Force Attack, PHI, Passwords, Passcodes, HIPAA, 256 Bit, Cryptography, Data Governance, SSN, DOB, Threat Actor, Identity Theft, Intellectual Property, Disaster Recovery, Spyware, Cybersecurity, CSO, Escalation, Encryption Services Team, Authentication Credentials, Sensitive Data Inventory, Rainbow Table Attack and Super Fun.
Cybersecurity Buzzword Bingo | DP-203 | Cybersecurity Buzzword Bingo | Cyber Bingo | Cybersecurity
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.