
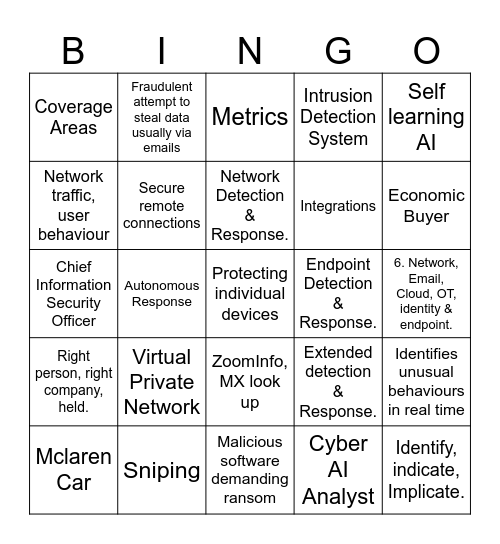
This bingo card has 50 words: Free!, Protecting individual devices, Security Information and Event Management, Malicious software demanding ransom, Virtual Private Network, Block unauthorized access, Fraudulent attempt to steal data usually via emails, Self-learning Artificial Intelligence (AI), Network traffic, user behaviour, Bring Your Own Device, Secure remote connections, Intrusion Detection System, Identifies unusual behaviours in real time, Extended detection & Response., Intrusion Prevention System., Identity & Asset Management., Network Detection & Response., Endpoint Detection & Response., Security Information & Event management., Self learning AI, Autonomous Response, Cyber AI Analyst, Coverage Areas, Integrations, Covering the entire attack life cycle, Identify, indicate, Implicate., Economic Buyer, Implicate Pain, Metrics, ZoomInfo, MX look up, Microsoft, Jill Popelka, Jon Gainey, 2013, Sniping, 75%, 2 or 3, 9000+, 92%, 6. Network, Email, Cloud, OT, identity & endpoint., 2400+, Cambridge & San Francisco, Azure, The POD., Mclaren Car, Chief Information Security Officer, Natural History Museum, 94%, Right person, right company, held. and Pain point & next steps agreed..
It's Security BINGO | Cloud Security BINGO | Cyber Awareness | Cyber Awareness | Intrusion and IDS Part II
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.