
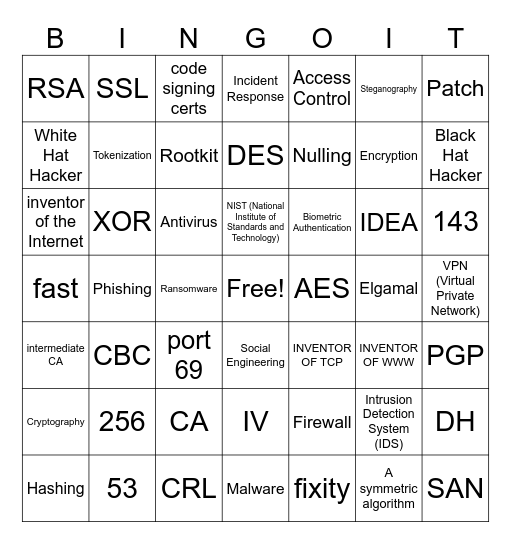
This bingo card has a free space and 48 words: Firewall, Encryption, Malware, Phishing, Antivirus, VPN (Virtual Private Network), SSL, 53, Steganography, Social Engineering, Patch, Incident Response, IDEA, Biometric Authentication, Cryptography, Elgamal, White Hat Hacker, Black Hat Hacker, Intrusion Detection System (IDS), Access Control, Nulling, Ransomware, RSA, Tokenization, DH, Rootkit, 143, Hashing, NIST (National Institute of Standards and Technology), XOR, A symmetric algorithm, AES, PGP, 256, fast, INVENTOR OF TCP, INVENTOR OF WWW, inventor of the Internet, port 69, CA, intermediate CA, SAN, code signing certs, CRL, DES, IV, CBC and fixity.
Let's Play EC Bingo! | Cybersecurity BINGO | CYBERSECURITY BINGO | I.T Bingo | Bitcoin and Cryptocurrency Review
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.