
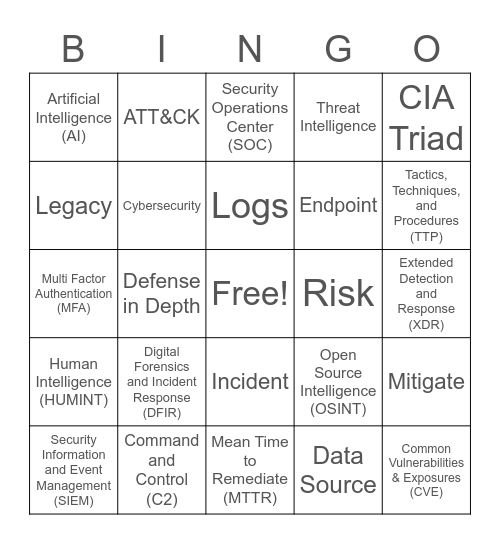
This bingo card has a free space and 43 words: Vulnerability, Common Vulnerabilities & Exposures (CVE), Continuous Risk Scanning (CRS), Security Information and Event Management (SIEM), End-Point Detection and Response (EDR), Data Source, Security Operations Center (SOC), Advanced Persistent Threat (APT), CIA Triad, Command and Control (C2), Threat Intelligence, Risk, Incident, Digital Forensics and Incident Response (DFIR), Penetration Test, Mean Time to Remediate (MTTR), Mean Time to Detect (MTTD), Multi Factor Authentication (MFA), Indicator of Compromise (IOC), Tactics, Techniques, and Procedures (TTP), ATT&CK, Machine Learning, Security Orchestration, Automation, and Response (SOAR), Artificial Intelligence (AI), Configuration Management Database (CMDB), Extended Detection and Response (XDR), Managed Detection and Response (MDR), Internet of Things (IoT), Open Source Intelligence (OSINT), Human Intelligence (HUMINT), Operational Security (OPSEC), Mitigate, Cyber Insurance, Defense in Depth, Ransomware, Malware, Zero-Day, Logs, Legacy, Endpoint, Exploit, Cybersecurity and Anti-Virus Software (AV).
Leading Ladies of the SOC BINGO | CyberSecurity Awareness - 2024 | SOC Ladies | Secureworks BINGO | Cybersecurity AI Awareness - Legal
Share this URL with your players:
For more control of your online game, create a clone of this card first.
Learn how to conduct a bingo game.
With players vying for a you'll have to call about __ items before someone wins. There's a __% chance that a lucky player would win after calling __ items.
Tip: If you want your game to last longer (on average), add more unique words/images to it.